Under the 'VMware Horizon Client for Mac' click the 'Go to Downloads' button. On the download page, browse to the bottom and click on the 'Download' button. When the download is complete, click on the Downloads button. Double click on the 'VMware-Horizon-View-Client' download. Tutorial: The following is a brief tutorial to walk you through the basics of VMware Horizon. This tutorial should take less than 5 minutes to complete. Open and log on to the VMware Horizon client by Double-Clicking on the VMware Horizon Client icon on your desktop. Double-click the desired desktop option and wait for the desktop to.
When I was still working as an Escalation Engineer for VMware® Global Support, there was a time-honored tradition among the Broomfield center's EUC support group: If you left your computer unlocked and walked out of eyesight, you'd always come back to a surprise. How do you paste a screenshot. The HR folks would probably be unhappy at such an unauthorized use, but a quick flip of the screen with Ctrl-Alt-Up and a dash back to your desk, leaving their display inverted and the surrounding engineers glancing over for the inevitable reaction, was worth the risk.
All the 'fun' of fixing your machine when you got back to your desk could have been prevented by hitting those three little keys we all know: Ctrl-Alt-Del. A quick press and the system is secured from any would be mischief-doers, and a smart Technical Support Engineer remembers this when he gets up from his desk in VMware GSS. We all do, or should, secure our system as a good habit when we step away, but when you're running a virtual machine, it can have an unintended consequence: the VDI session can also receive this keystroke and act on it. What is the best word processing program for mac.
A colleague recently came to me with a question from his customer: Is it possible to script it so that VMware Horizon® Client for Windows would behave similarly to the Linux client when handling Ctrl-Alt-Del and Windows-L? That's a loaded gun ready to fire, for those in security call this something: malware—bypassing the kernel is a big taboo. Of course, there are those thinking, 'Mike, this is easy, just use the PCoIP Session Variables to block the keystroke!' And you'd be right, with PCoIP, but few actually sit down and ask the simple question familiar to childhood, 'But . . . why?'
Adobe clip for mac. Secure Attention Key (SAK)
First, for some context, let's take a little trip down the rabbit hole of operating-system design. In all modern operating systems, there is something called the Secure Attention Key (SAK), which can be invoked by the user. It is an old concept originating in the early 1990s, when stealing someone's password wasn't typically a malicious act, rather a display of your prowess. By simply showing you could, it was known that your skills with the infrastructure of the day were sound. The forward thinkers of the world concluded that a user should definitively know that the screen they were about to enter credentials into was that of a trusted security subroutine and not a fake.
Almost a funny notion these days of ever-increasing security, but from it we were left a legacy in the familiar keystrokes we still use to get into our operating systems. It varies between operating systems, but the principles of operation are the same, be it Windows or Linux. Now, there are endless debates on the usefulness of the SAK and whether it truly increases security in the modern era, but, for our purposes, the story of its origins is important to answering my colleague's question because the SAK defined the keystrokes we use today.
In that proverbial Paleolithic period of IT that is now the NT days (my, how far we have come), the engineers sat down to find a keystroke that could be used by the security subsystem, too. After much discussion, it turned out that one single keystroke wasn't in use for another purpose within the operating system itself: Ctrl-Alt-Del. Before that, Ctrl-Alt-Del had humbly succeeded its predecessor Ctrl-Alt-Esc on the original IBM PC keyboard. It was an excellent combination, insofar as it would save the clumsier (or angrier) of us from accidentally (intentionally) bumping (slamming a fist into) the Ctrl-Alt-Esc and rebooting the machine leading to (more) frustration. So, Ctrl-Alt-Del was enshrined within Windows NT 3.1 as the Secure Attention Key, a proud tradition that we carry on in the 21st century.
Horizon Client Behavior on Linux and Windows
With that history and humor in mind, let's look at the answer to my colleague's question from two different Horizon Client–side operating systems: Linux and Windows, specifically what happens on those systems in context with the behavior of the Horizon client. https://downbload797.weebly.com/slots-plus-no-deposit-bonus-codes-2017.html.
Linux has two attributes that are very important, and put a quick end to the issue of Ctrl-Alt-Del:
- The SAK keystroke is usually Break-K or Ctrl-Alt-Pause.
- The somewhat cliché adage, 'Everything is a File.'
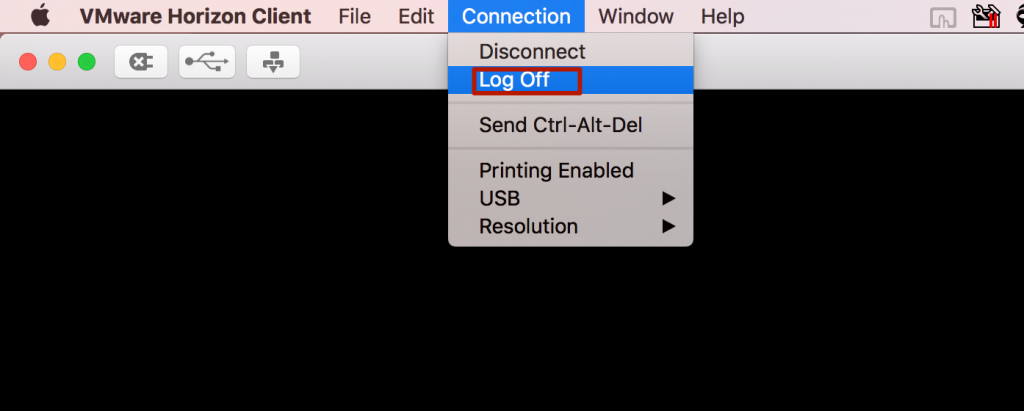
Vmware Horizon Client Send Ctrl Alt Del
That combination makes for a very easy workaround which you can find in the following document at the bottom of page 39: https://www.vmware.com/pdf/horizon-view/horizon-client-linux-document.pdf Simple, effective, and also leaves more options on the table. There are a lot of flavors of Linux, and it can be customized to do basically anything you'd like, but in general, the more popular flavors have designed Ctrl-Alt-Del to bring up a Task Manager.
Vmware Send Ctrl Alt Del
Windows is a bit different. In your standard Windows Client to Windows VDI scenario, the Secure Attention Key is the same on both ends. In Windows, when the Secure Attention Key is invoked, there are different actions invoked by the kernel; we are only concerned with the happenings after a user is logged in, which is the invocation of Windows Security. From its humble origins, it has evolved into the familiar screen with options to lock, sign out, change your password, call up the task manager, and (in the XP successors) switch users. Mac studio fix powder foundation routine. Importantly, Windows-L also invokes the Windows Security process, but to directly lock the system rather than present the familiar menu.
The important takeaway is that when this key is pressed, only one thing in the computer has the authority to intercept it: the kernel. There are, of course, ways to subvert the kernel and intercept the keystroke, but for malicious software that has made it to that point, intercepting a user's password is inconsequential since, for all intents and purposes, it is the system at that point.
And so it is we return to my Technical Support Engineer from above. When he locked his machine with the intention of ensuring he didn't return to a Justin Bieber background, he forgot that this was going to lock his VDI session as well. In the grand scheme of the universe, this is a minor inconvenience, but in our modern age of ultra-low latency systems that can render a 4K display at 60+ FPS and serve up the world at your fingertips, most end-users find it to be a near capital offense on the part of both the computer as well as the VDI Administrator that put it in front of them.
The Mighty Keystrokes
In closing, if you're using PCoIP, setting the PCoIP session variables to block Ctrl-Alt-Del is a simple thing, and the PCoIP engine will dutifully ignore the input and not relay it to the VDI OS's kernel. Otherwise, it comes down to user training to click through the appropriate invocation of Lock via the Start menu of the version of Windows they are running. It won't hurt to let them know they aren't alone, and even we at VMware occasionally run afoul of the all-powerful Windows Security and its mighty keystrokes.
Welcome to VMware Fusion® documentation. Use the navigation on the left to browse through documentation for your release of VMware Fusion. We update the online documentation with the latest point release information. For example, version 10 contains all the updates for 10.x releases. All our documentation comes in PDF format, which you can access by selecting the PDF download icon while reading a page or viewing a search result.
If you want to learn more about what Fusion does and how it can help you run your Windows and Linux applications on your Intel-based Mac, visit the Fusion product page. To view or ask questions about Fusion, visit the VMware Fusion Community.
Supplementary Resources
The following video describes what is new in Fusion 10.
